Anticipate Risks Through Comprehensive Privacy Threat Modeling
What You Don’t Know Can Hurt You
The only way to reliably guard against privacy risks is to use a systematic approach to uncover and address these risks wherever they may be found in your company’s product, service, or process. This approach is called Privacy Threat Modeling, and it’s a vital part of the comprehensive procedure we use to fortify your company against todays threats and tomorrows.
Our specialized expertise will navigate you through the intimidating unknown, highlighting — and resolving — specific privacy risks so that your company can continue to be a name your customers trust.
Privacy Threat Modeling
Step 1 - Identify the Potential Privacy Harms
In order to protect individuals from privacy harms efficiently, it’s first necessary to understand what constitutes a “privacy” harm. While there are many resources that can help identify specific harms, we rely heavily on Daniel Solove’s ‘A Taxonomy of Privacy’ for its well-regarded, comprehensive, and granular articulation of behaviors society widely views as privacy violations. Using the Taxonomy, we look at your current product, service, or process and identify the ways in which any of these harms could materialize.
Step 2 - Identify the Actors Involved and Their Roles
Who needs to be protected from a potential privacy harm? Your employees? Your customers? In what context? Moreover, who are the potential perpetrators of a privacy harm? An external hacker? A vendor? Or even an internal department? We’ll ask the necessary questions and uncover the answers.
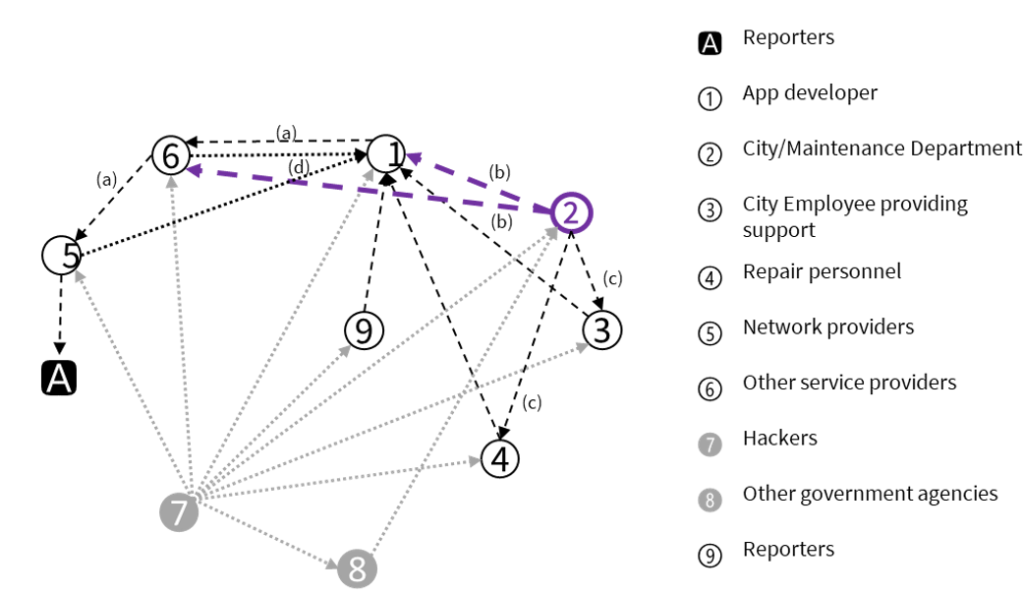
Step 3 - Identify the Interactions Between the Actors
We’ll closely analyze the relationships within your business operation and zero in on the opportunities for privacy harm. The diagram below provides an example of the complexity often involved in a company’s network of relationships.
Step 4 - Identify the Specific Ways A Perpetrator Could Carry Out Privacy Harms and How These Actions Could Threaten At-Risk Individuals
The last step of this process involves looking more closely at the actors and the privacy harms they could suffer or commit. More specifically, we would assess how would-be perpetrators could cause harm. Could they act directly, by proxy, or through an intermediary? If through an intermediary, who? What harm would result? Armed with this insight, we can suggest changes to eliminate threat opportunities, conduct further risk assessments to understand the likelihood and severity of those threat opportunities, or implement other controls to limit associated risks.
Contact us today to discuss in-person or online speaking engagements.
Interested in learning more about Privacy Threat Modeling? Check out our training website for a list of courses on this and other topics to boost your privacy program!
Schedule a Consultation
Privacy should always be a guarantee… together we can make it so! Your contact information will only be used to discuss potential services with you.
